Artificial intelligence
A comparison of classic algorithms and artificial intelligence for error detection in V2X data shows: The improved results of AI come at a high price.
SDV
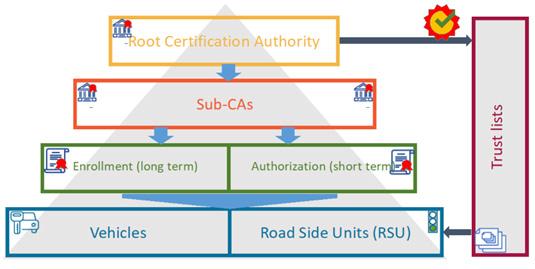
Trust on a global level is not enough. Explore with us how your vehicles can trust data received via V2X.
SDV
The goals of V2X include improving safety and trust in road traffic. Discover how this works on a global scale and why it is not enough on its own.
Data-based ecosystems, SDV
The development of highly complex driving functions for autonomous driving requires improved sensors and optimized data use in the collaboration between automobile manufacturers, sensor suppliers and simulation development. Data ecosystems in conjunction with digital twins offer an efficient solution for safe and cost-effective updates.
SDV
Join us for an in-depth look at the challenges and opportunities for ADAS in the backend and find out why providing additional information for ADAS functions is so crucial.
SDV, Quantum Computing
Experts assume that information security will be threatened by quantum computers in the future. With the right action plan, companies from the IIoT, automotive and KRITIS sectors can prepare themselves today for the use of new encryption technologies and thus mitigate the risks posed by quantum computers.
SDV
Modern vehicles are equipped with an increasing number of automated driving functions. How can external data increase the safety level without compromising functional safety?
Data-based ecosystems, SDV
The close interaction between hardware, software and data in the vehicle opens up new opportunities for car manufacturers.